Abdallah Mohammed (1bdool492)

About Me
Cybersecurity professional with 4+ years of hands-on experience in penetration testing, bug bounty hunting, and security consulting.
Recognized by leading global organizations for identifying and responsibly disclosing critical vulnerabilities. Ranked among the top security researchers on HackerOne with 700+ valid reports submitted across various programs.
Specialized in Web, Mobile, API, and Network penetration testing with expertise in OWASP Top 10, MITRE ATT&CK frameworks, and modern exploitation techniques.
Achievements & Rankings
Competitive rankings and recognition in the cybersecurity community
Hall of Fame
Recognized by 78+ major organizations worldwide
Professional Experience
Kliotech Security
Penetration Tester
Resecurity (Part-Time)
Cybersecurity Researcher
HackerOne (Freelance)
Bug Bounty Hunter
Bugcrowd (Freelance)
Bug Bounty Hunter
BugBountySA (Freelance)
Bug Bounty Hunter
Yogosha (Freelance)
Bug Bounty Hunter
Certifications

OSCP
Offensive Security Certified Professional
Offensive Security
OSCP+
Offensive Security Certified Professional Plus
Offensive Security
eCPPTv2
Certified Professional Penetration Tester v2
INE Security (eLearnSecurity)
eMAPT
Mobile Application Penetration Tester
INE Security (eLearnSecurity)
eWPTv1
Web Application Penetration Tester v1
INE Security (eLearnSecurity)
CSCRB
Certified Security Code Review - Beginners
Red Team LeadersTools & Skills
Private Tools
Custom-built reconnaissance & vulnerability scanning tools
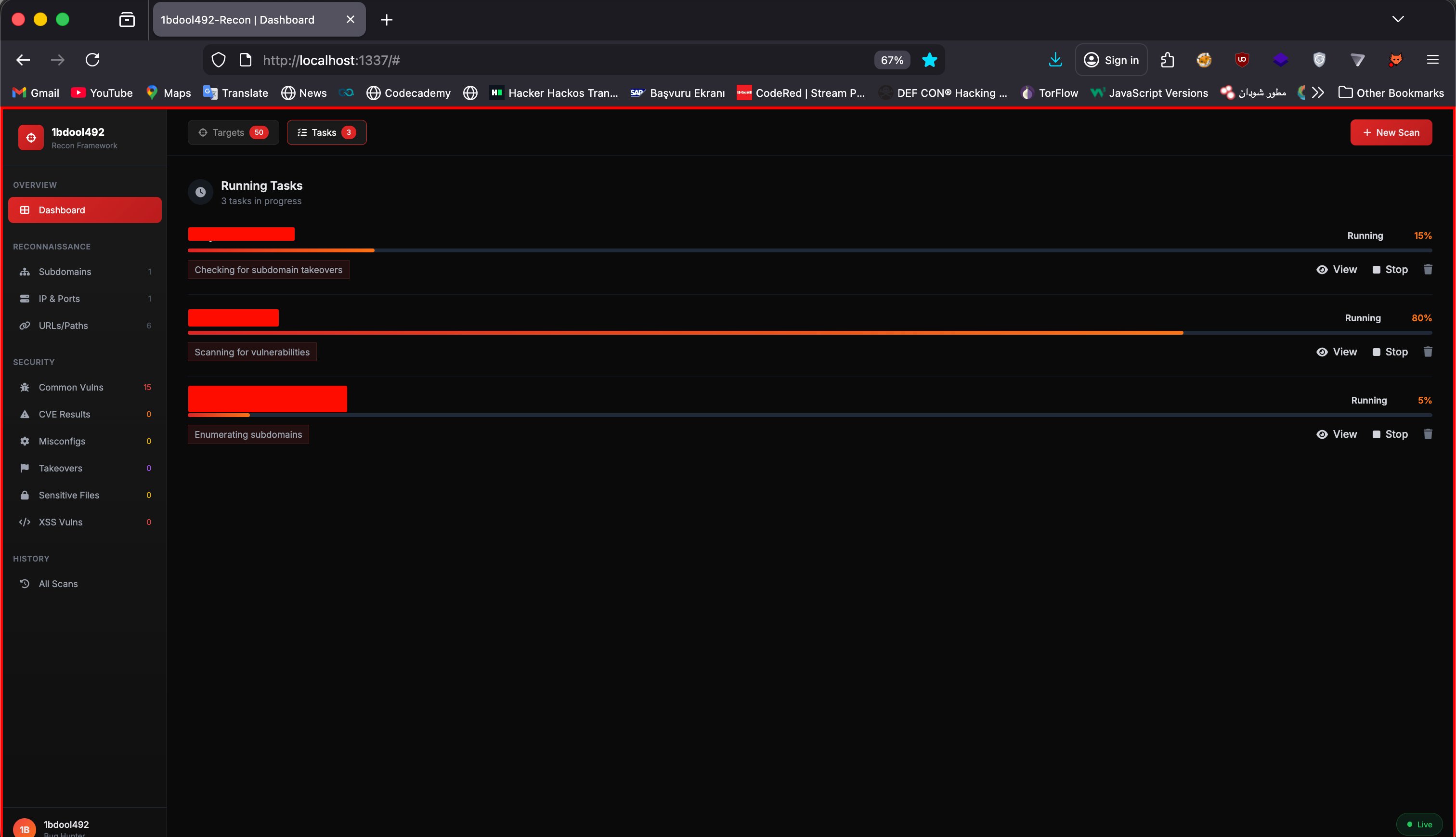
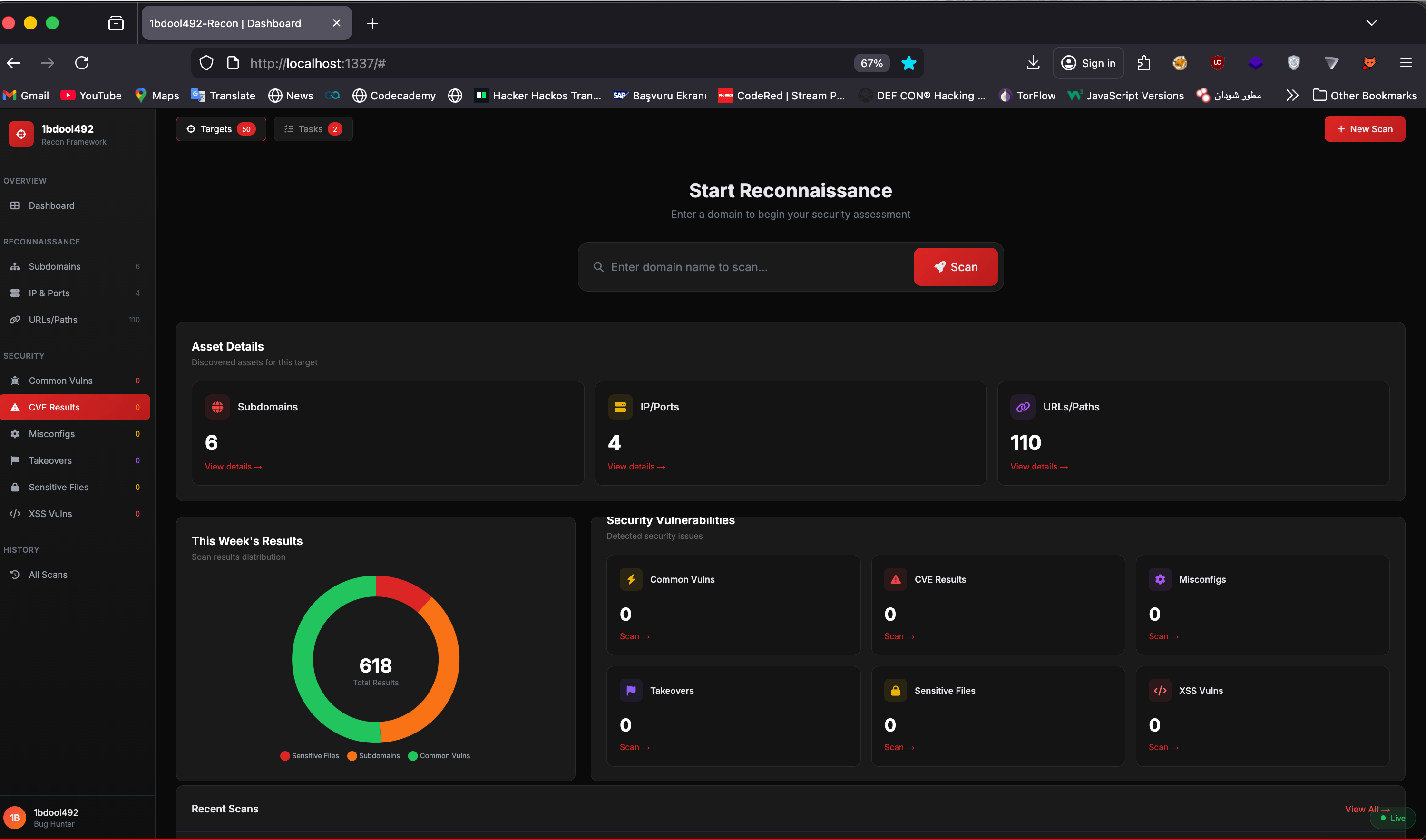
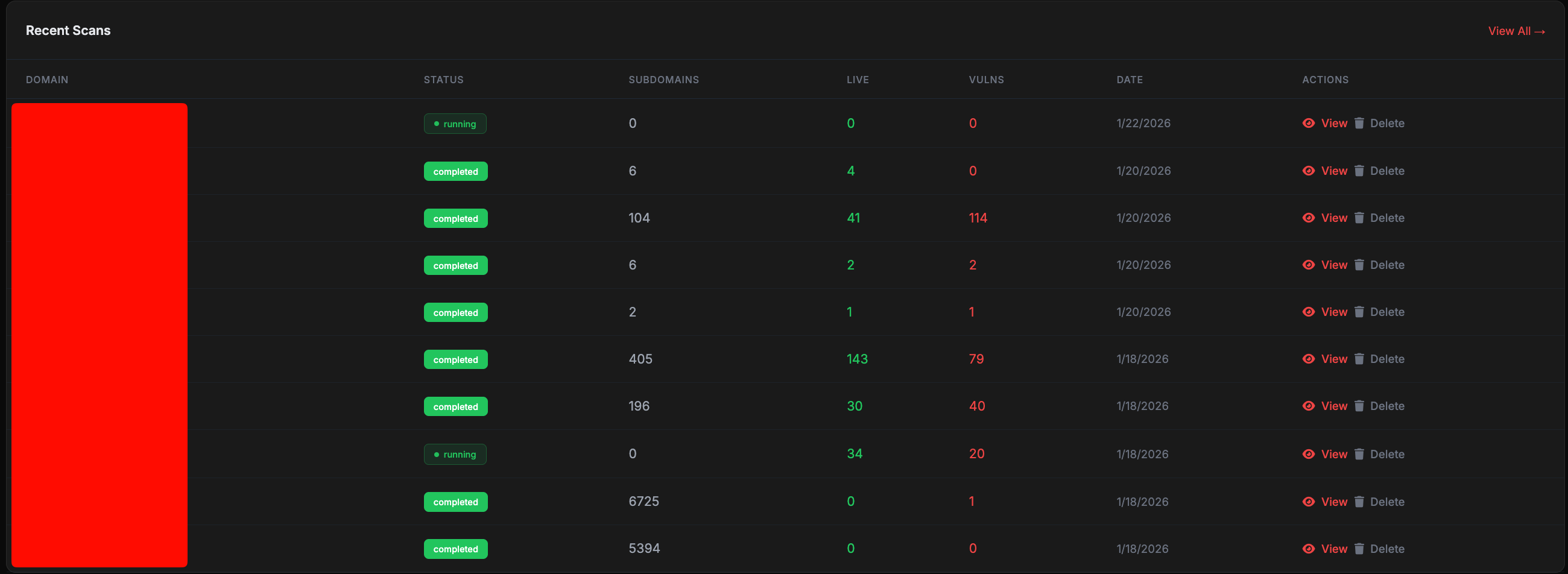
1bdool492-recon
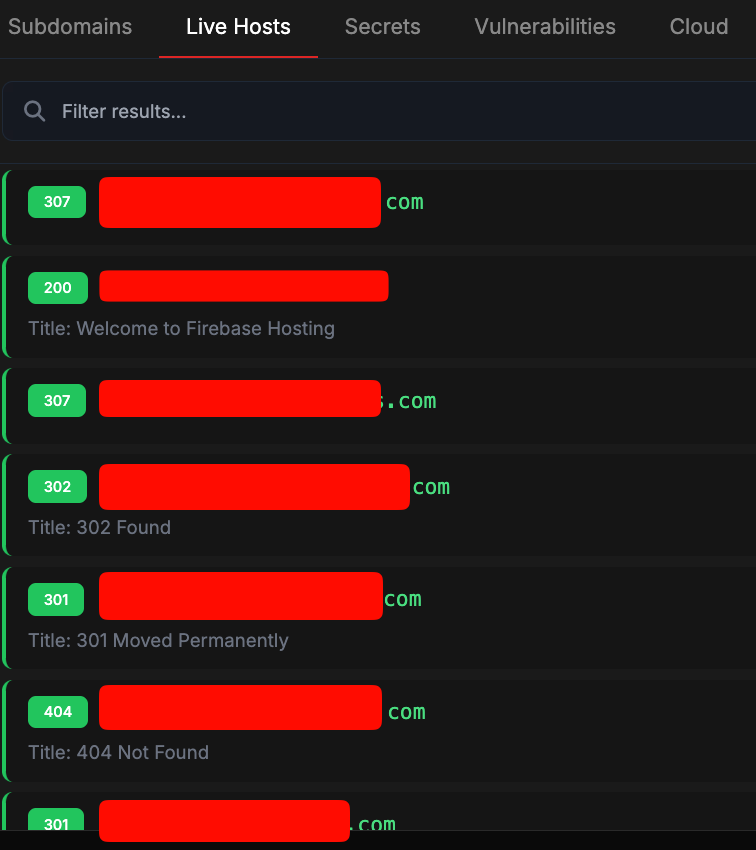
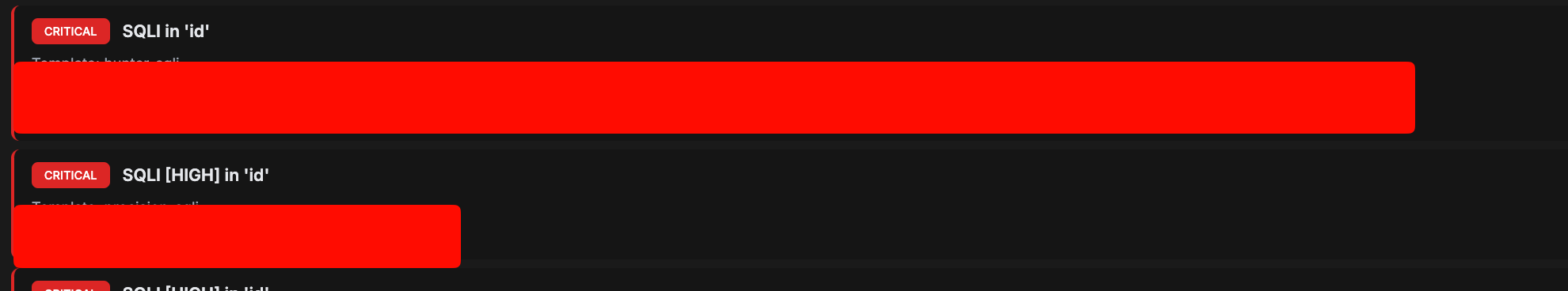
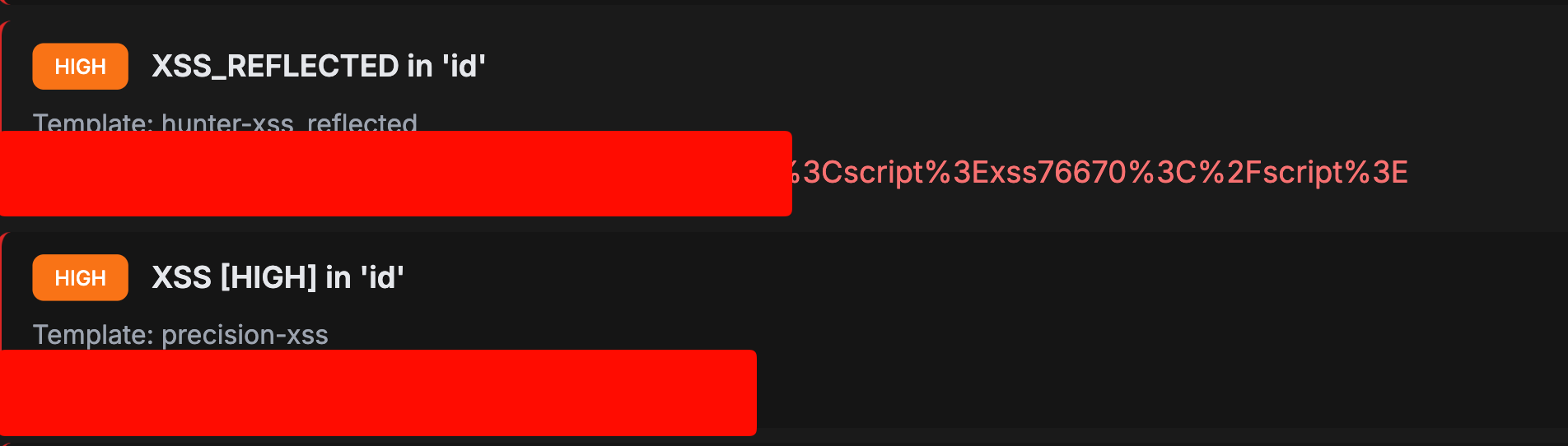
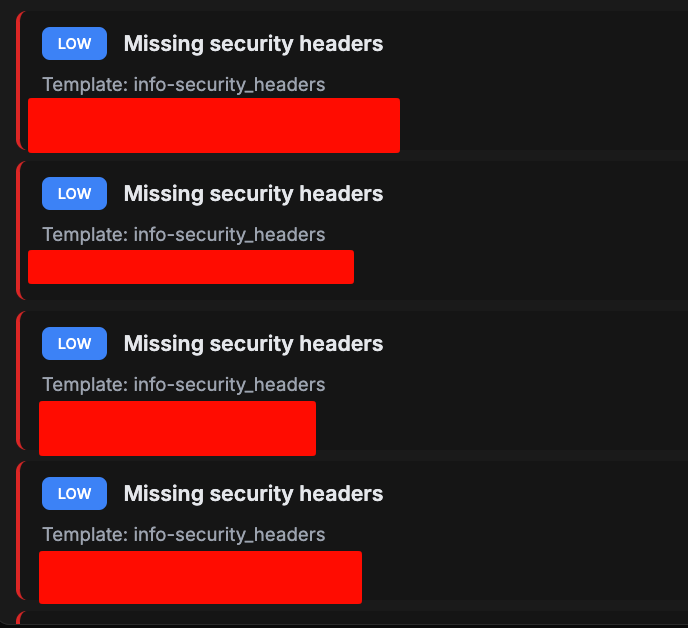
PrivateAn advanced automated web reconnaissance and vulnerability scanning framework. Features include subdomain enumeration, port scanning, directory bruteforcing, technology fingerprinting, and automated vulnerability detection. Built for efficient bug bounty hunting and penetration testing workflows.
Contact Me
/usr/bin/message



